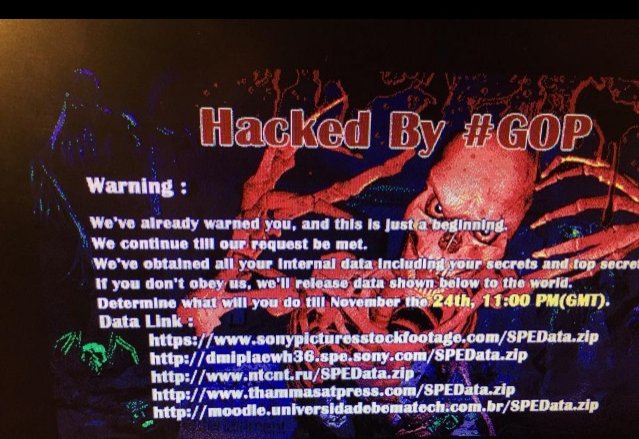
On Monday, employees at Sony Pictures Entertainment—the television and movie subsidiary of Sony Corp.—discovered that their internal corporate network had been hijacked. A message from an individual or group claiming responsibility appeared on corporate systems, pledging to release sensitive corporate data taken from the network by 11pm GMT on Monday.
Twitter accounts associated with promoting several movies, including Starship Troopers, were briefly hijacked by the attackers. The attackers posted to at least three Twitter feeds, leaving the same message: “You, the criminals including [Sony Pictures CEO] Michael Lynton will surely go to hell. Nobody can help you.” The image posted with the message shows a digitally edited image of Lynton’s head in a dark, hellish landscape.
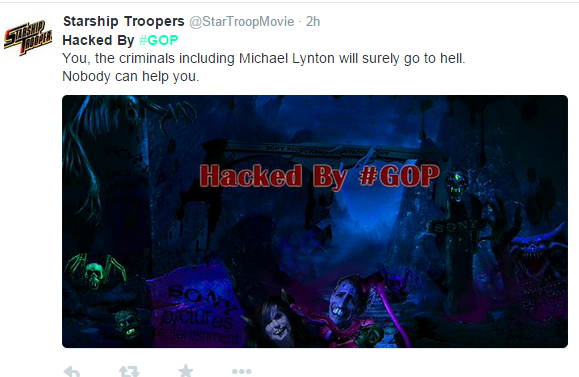
As of this morning, the network at many Sony offices still appears to be down. Based on information reportedly shared by employees, it could be down for weeks before being restored. The Twitter accounts appear to be back under Sony Pictures’ control.
Meanwhile, at least some of the data that hackers purportedly used to extort Sony has been released—and has been pounced upon by some reddit users who have started to analyze its contents. So far, a reddit thread on the breach claims to have found files containing passwords, files apparently named to provide password hints, copies of the passports of some actors attached to Sony films, and maybe even some pirated movies from companies other than Sony.
There were some questions whether this was a hack at all. So far, all Sony has said is that the company is investigating an “IT issue.” However, the file that the hacker or hackers—who call themselves “The Guardians of Peace”—have released is a 217.6-megabyte .ZIP file that contains three text files, two of which allegedly contain lists pulled from Sony Pictures systems.
“These two files are the lists of secret data we have acquired from SPE,” said the text in a file called readme.txt. “Anyone who needs the data, send an email titled °∂To the Guardians of Peace°∑ to the following email addresses.” A list of e-mail addresses through anonymous mail services Yopmail and Disgard.email followed.
The files containing the list of data allegedly gleaned from Sony Entertainment’s network contain about a gigabyte of dumped text (638.4 and 397.8 megabytes, respectively). Included in the list:
- PDF files that apparently contain the passports, visas, and other associated identity documents of cast and crew for various Sony productions, such as actors Jonah Hill, Cameron Diaz, and Angelina Jolie (plus a file called Emmerich, Roland Greencard.pdf).
- Over 700 documents containing passwords, including spreadsheets and Word files titled “FTP passwords,” “ResearchPasswords," “ACCOUNTING PASSWORDS,” “Personal passwords,” and other files named for specific creative resource sites. There is also a file called “CA Breach Notification for User Names and Passwords (MoFo).pdf,” which someone at Sony will likely be referring to shortly.
- 179 Outlook archival .pst mailboxes, including the mail folder of an executive at Sony Pictures Releasing Canada, an IT Audit Supervisor at Sony, as well as many “archive.pst” and “backup.pst” files.
- Password protected documents—with their passwords in their names. (PASSWORD PALABRA SECRETA NISSAN.xlsx, PwC 2007 Report_PASSWORD_pwcemc60.pdf).
- IT audit documents (PASSWORD EQUAL TO USER NAME.xls, ACCOUNTS WITHOUT PASSWORDS.xls).
- Sensitive business documents including film budgets (“JR_Accrued Mktg Cost 0513 - Evil Dead.xls”) and contract documents (“Cameron Diaz - Pre-approved Medical Rider.doc”).
- Personal credentials including private key files and 1Password database backups.
- Media files for television shows that aren’t Sony Pictures products and may have been pirated copies on an employee's desktop:
Adventure Time-2x04a-Power Animal.avi
Adventure Time Her Parents.avi
Adventure Time The Silent King.avi
Adventure Time-2x09b-Susan Strong.avi
Adventure Time-2x11a-Belly of the Beast.avi
Human.Planet.S01E05.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E02.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E06.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E03.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E04.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E01.720p.BluRay.x264-SHORTBREHD.mkv
Human.Planet.S01E07.720p.BluRay.x264-SHORTBREHD.mkv
The extent of the files suggests that the attackers gained access to backups of individual computers as well as SharePoint servers, file servers, and other significant pieces of Sony Pictures’ infrastructure. Considering how broad and deep the exposure appears to be, Sony Pictures’ IT team may especially want to get to two files listed in the file-name dump: “INSURANCE for security breaches.doc” and “Security Breach Course of Action.v1.txt”.
reader comments
107