
Symantec Security Response has observed a new variant of ransomcrypt malware which is easy to update and uses open source components to encrypt files. The variant, detected as Trojan.Ransomcrypt.L, uses a legitimate open source implementation of the OpenPGP standard to encrypt files on the victim’s computer. The threat then displays a ransom notice in Russian, asking the user to pay in order to unlock the files.
This isn’t the first time we’ve seen malware authors using open source encryption components in their ransomware threats, but it does show a continuing trend of attackers making ransomware easier to create and maintain. While ransomware can typically be complex, the malware author for Trojan.Ransomcrypt.L made the threat easy to develop and maintain.
Using GnuPG to take files hostage
Trojan.Ransomcrypt.L uses GnuPG, an open source implementation of the OpenPGP standard. This implementation was designed to allow users to encrypt and sign their files and manage the keys needed to unlock these files.
The malware’s main module is a batch file, allowing the attacker to control the threat’s behavior and easily update it. Thanks to this batch file, the malware can simply execute a command to encrypt files on the victim’s computer.
The threat downloads the 1024-bit RSA public key and imports this key through an option in GnuPG. The malware then encrypts the victims’ files by using GnuPG’s Encrypt Files option with the public key. If the user wants to decrypt the affected files, they need the private key, which the malware author owns. It’s difficult for victims to decrypt the encrypted files without this private key.
After the Trojan encrypts the files, it opens a text document containing a ransom demand in Russian. The ransom demand asks the user to pay a minimum of €150 (just over US$200) in order to get the key to unlock the files.

Figure 1. The ransomware’s warning
Author’s appreciation for open source tools
The malware author also included a message of appreciation for the open source components in the malware.
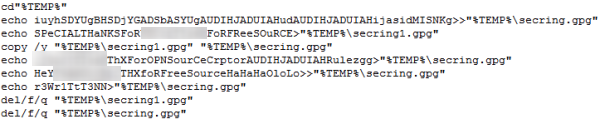
Figure 2. The appreciation message included in the batch file
The author wrote the following messages in one of the malware’s files named %Temp%\secring.gpg.
“Special thanks for [REMOVED] for free source”
"[REMOVED] thx for opn source cryptor"
“Hey [REMOVED] thx for free source, Ha Ha Ha, lol”
However, the malware author has since removed these messages to prevent users from seeing them.
Protection
The ransomware uses the public key cryptosystem so the encrypted files cannot be decrypted easily without the private key.
Symantec detects this threat as Trojan.Ransomcrypt.L. Keep virus definition up to date to stay protected against this threat and back up important files frequently so that they can be restored at a later date. Never pay the ransom to the attackers – remember, there’s no guarantee that the attackers will provide the key to unlock the files.