
Researchers have uncovered yet another Android-based adware campaign targeting people who download what they believe are trusted titles from websites and other third-party app stores.
The apps use repackaged icons to disguise themselves as popular titles and are offered for download through pop-up ads on visited websites and in-app promotions, according to a blog post published Wednesday by researchers from security firm FireEye. Once installed, the apps exploit as many as eight separate Android vulnerabilities that allow the apps to gain deep root access privileges. From there, the apps launch code libraries mimicking legitimate Android services, such as com.facebook.qdservice.rp.provider and com.android.provider.setting, to gain a permanent foothold on infected phones.
FireEye researchers wrote:
This malicious system service contacts aps.kemoge.net for commands. To evade detection, it does not constantly communicate to the server. Instead, it only asks for commands on the first launch or after 24 hours from its last command. In each communication, it first posts the IMEI, IMSI, storage info, and installed app info to the remote server. We intercepted the network traffic on a Nexus 7 with Android 4.3 and with the first sample listed in Appendix I installed. The corresponding traffic is shown in Figure 7. After uploading the device info, it asks commands from the server, as shown in Figure 8.
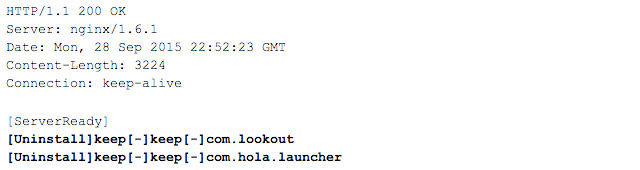
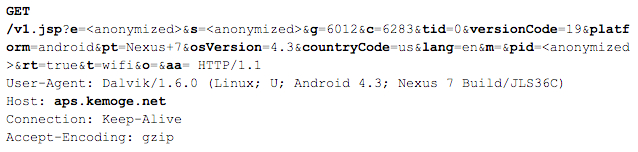
Figure 7 is notable because it shows the code using its root access privileges to uninstall the legitimate Lookout antivirus app, possibly in anticipation of further attacks FireEye has not yet seen. One of the samples observed by FireEye is also notable because it was signed by the same developer certificate as an app recently found in the official Google Play store. While the app available in Google Play didn't contain any malicious functionality, more nefarious functions could be added on the fly by one of the servers the app connects to, FireEye said. Google has since pulled the app.
The FireEye blog post is another reminder of the threats that come from Android apps available in third-party app stores. No doubt, Google's security vetting of apps is by no means perfect, but it does offer a level of protection that's generally not available elsewhere. Android users should make use of it whenever possible and remain highly suspicious of other sources.
reader comments
103